Technology of counteraction to falsification of credit cards
Date: February 12, 2004Source: Homepage
By:
The counteraction to methods of a falsification paper, and recently and plastic, documents is a traditional and urgent task of protection of carriers of the information. One of key elements for many documents is the photo. It is possible to not speak what economic and legal harm the falsification of photos puts. Such documents as the passport, driver's certificate, credit or identification card, medical policy and others here concern.
Alongside with cryptographic by methods of protection of the information the large meaning get steganographic, i.e. methods of concealment of the fact of the information transfer. One of such methods of introduction of the latent water marks is fixed in a basis of the present technology. The offered technology represents a combination steganographic of the approach of concealment and cryptographic of the approach of the data enciphering, that provides practical impossibility of breaking.
It is possible to present the design of identification process, for example of owner ID of a card, as set program and means working as a mode of real time:
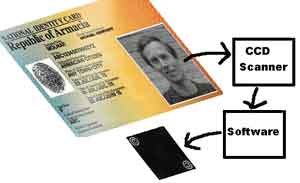
The photoimage is read by the CCD-scanner, is exposed to transformations for detection of a water mark, and then the water mark is shown on the monitor. In figure, the water mark is submitted as a mark copyright.
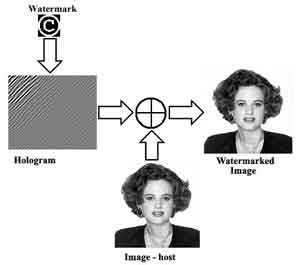
This resource illustrates technology of protection of the documents photographic on a paper or plastic basis. In a basis of technology of introduction of the latent water marks the holographic principle is used. Essence of a principle is the synthesis of the digital hologram of a water mark and additive mixing of the hologram with the host-image:
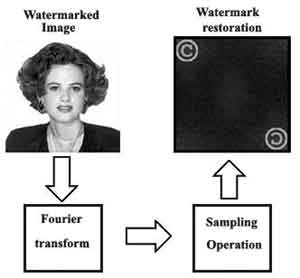
For realization of return procedure (procedure of restoration water), it is enough to execute Fourier transformation. The digital signal processors (DSP) of firm Texas Instruments allow to execute this procedure for shares of second. During restoration of a water mark, it is possible to observe as restored object, and its holographic image:
Major element of any information system is enciphering the confidential information. The considered approach is not exception. The two-dimensional cryptogram integrally are built in a chain of transformations of the two-dimensional images:
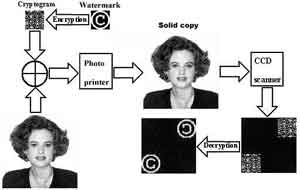
The stability of the code is determined by extremely stability of a confidential key. Cryptographic a subsystem and Steganographic system of concealment of the data are practically insuperable barrier for non-authorized breakings.
 Add comment
Add comment
 Email to a Friend
Email to a Friend
